In part 2 of our series on secure torrent downloading, it’s all about lawsuits, warning letters and all the bothersome legal problems you read about all the time in the press. You will learn what the exact dangers are, and why we strongly advise you to use protection.
[alert type=”info” close=”true” heading=”Important Disclaimer”]Remember that it is your sole responsibility to comply with your countries laws. Privacy is not a crime, and you have the full right to use the BitTorrent network anonymously to download the files you’re allowed to without being harassed or tracked by anyone. Anything else is your business, not ours. Consult our article on what is legal and what isn’t in case you’re unsure. [/alert]
First of all, remember that BitTorrent in itself is completely legal, only certain content that can be found is not legal to download without permission of the copyright holder. In the first few years, it was completely safe to get whatever you wanted, and nobody bothered to spy on the network.
Enter the copyright industry with all their political power.
Now, providers and universities keep track of their customers and send them “warning notices”, “informing” them about suspicious activities originating from their IP (an unique identifier allowing to track down every Internet user), threatening with disconnecting you or slowing your bandwidth down.
Worse, a whole armada of tracking companies keep a constant eye on the network and issue mass lawsuits against users, basically extorting you into paying a few hundreds to several thousand bucks unless you want to be dragged into court.
Their methods? Dubious. Errors are rife, with people reportedly not even at home or on vacation while the alleged copyright violation happened, or getting sued for downloading freeware, software that can legally be shared with anyone by any means. [line]
The two basic methods to “track” users:
[dropcap]A[/dropcap] surveillance company targets a torrent and joins the party, behaving like a regular user. Because in a torrent network, anyone can see the identity of everyone also downloading the same file, they can pick out as many users as they like. Since your torrent client not only downloads but also shares pieces of content with others, they can not only sue you for downloading but also for distribution.
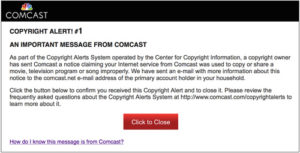 In the next step, either a notice is send to your provider that sends you one of said “notices”, or a lawsuit is filed against you, forcing your ISP to give them your personal data, read your name and address. An associated law firm then sends you one of the dreaded “pay-up-or-else” letters you hear so much about in the news, and ignoring them only increases the sum you’ll have to pay if the matter goes to court. Learn more about the scheme and the so-called “evidence” here.
In the next step, either a notice is send to your provider that sends you one of said “notices”, or a lawsuit is filed against you, forcing your ISP to give them your personal data, read your name and address. An associated law firm then sends you one of the dreaded “pay-up-or-else” letters you hear so much about in the news, and ignoring them only increases the sum you’ll have to pay if the matter goes to court. Learn more about the scheme and the so-called “evidence” here.
Of course, while your ISPs warning notices aren’t fun at all and can have very unpleasant consequences, they’re essentially harmless compared to the second possibility.
[line]
[dropcap]I[/dropcap]t is also possible to analyze the traffic going in and out of your computer and detecting if you use file sharing applications. Some ISPs actually do that to “preemptively” warn users, but it is even more common in your school, university or employers network. Many of these more or less public networks forbid any P2P/BitTorrent activity and will act against you if you do it anyway.
This kind of tracking is very difficult to circumvent with traditional methods like proxy servers, but we also consider it dangerous for you, no matter if you share files or not. The last thing you want is your traffic being monitored by somebody, like you wouldn’t like anyone to read your letters and messages to loved ones.
[line] [content_band inner_container=”true” no_margin=”true” border=”none, top, left, right, bottom, vertical, horizontal, all” padding_top=”40px” padding_bottom=”40px” bg_pattern=”” bg_image=”” parallax=”true” bg_video=”” bg_video_poster=””]Protection Methods: How To Reclaim Your Privacy
The best and easiest solution: A VPN service such as HideMyAss encrypts your data and hide your identity, completely “blinding” anyones attempt to see what you do or who you are.
Other possibilities include, for example, using public WiFi networks (consult this article for a complete overview), but a VPN is by far better in several aspects. Basically it is an encrypted tunnel through which all your communications between you and the Internet are send, with the VPN service swapping your identity against a new, anonymous one of the other side.
[prompt type=”left, right” title=”Our Guide On How To Use A VPN” message=”Read our review of the best and most convenient services, along with detailed guides on how to set them up. It takes about 5-15 minutes to set the whole thing up, and you can feel much safer again.” button_text=”Click me, now!” href=”” target=”https://www.theloadguru.com/vpn-the-best-services-and-how-to-use-them/”]
This completely blocks anyones attempt to see what you are doing by snooping through your traffic, and new IP ensures no one can track down who you are. A good VPN service will either simply not keep any logs of which user was behind which identity, or have a very strong privacy policy ensuring no information is given to third parties.
And best of all: Setup is so easy anyone can do it in about 5 – 20 minutes, and speeds are very high so you will very likely not even notice the VPN is activated.
Note however that not all VPN services are created equal, as they are big differences in pricing, privacy policy and software. Check out our article “How to Use A VPN For Anonymity And Unrestricted Internet Access” for more information.
[/content_band]



